Janus Digital Signage.
Deliver engaging communications from a trusted, secure CMS
A specialist digital signage solution designed to drive engaging communication across an entire property by connecting content, integrating existing applications and simplifying content management. Janus is a secure, all-in-one platform for any display application. A tried, tested and trusted platform that enables the delivery of connected content from our CMS to digital signage displays, video walls, secure workstations, digital menu boards, interactive wayfinding screens, and much more.
Connected content, deployed everywhere
Janus hotel digital signage is both as powerful and as simple as you need it to be. Drive templated content to a single
endpoint or scale seamlessly across an entire enterprise with 1,000s of players and multiple concurrent users.
Communicate key messaging
Integrate with real-time feeds to display weather, local attractions, flight and shuttle schedules, and other convenient information that improves operations.
Promote your property
Control localized promotional communication to drive adoption and utilization of on-site amenities, loyalty programs, add-on services, and more.
Engage your audience
Strengthen the connection with guests and staff through video, digital art, personalized entertainment, interactivity, live TV, and targeted content.
Digital signage connected by a powerful CMS
What good is a hotel digital signage system if it doesn’t fit seamlessly into your day- to-day operations? With Janus you enjoy simple customization, scheduling, monitoring, and deployment of content across all digital signage displays.
Share high-impact content experiences that drive guest loyalty and revenue and strengthen connections with your staff.
Our Content Management System ensures there is a solution matched to your needs — from a single admin to a 24/7 enterprise network.
Signage solutions to connect your entire property
Choose a single hotel digital signage option or implement a combination of digital communication solutions, either is flexible enough to evolve with your hotel.
Topic Boards
Digital Concierge

Menu Boards
Wayfinder
Shuttle Tracker

Video Walls
Topic Boards
Set it and forget it. Pick your combo of content, we’ll do the rest.
Travel Boards
Provide guests with real time flight tracking, weather and traffic conditions to make their journey and travel experience flawless.
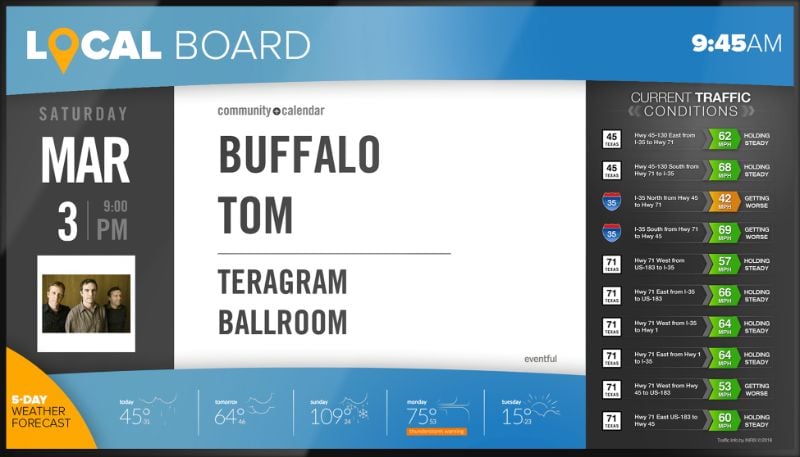
Local Boards
Display local attractions, event listings, weather and more to help guests become fully immersed with the local community.
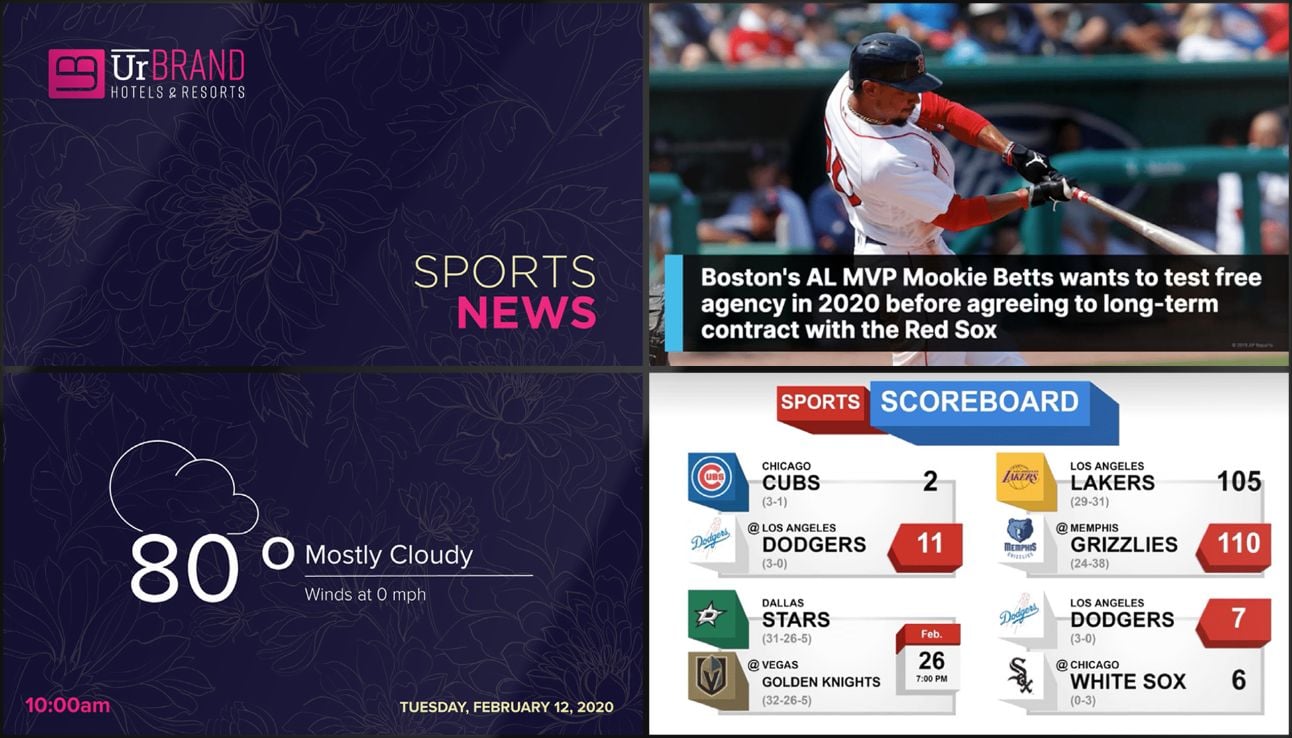
Score Boards
Keep your guests up to date and informed of the latest sports scores, upcoming sporting events, and sports related news feeds.
Health Boards
Keep your health conscious guests aware of the latest health news and display pertinent warnings.
Custom Topic Boards
Combine one or more content widgets to design your own personalized
informational sign. Don’t see something you want to display? Simply share your vision with our team and we’ll bring it to life.


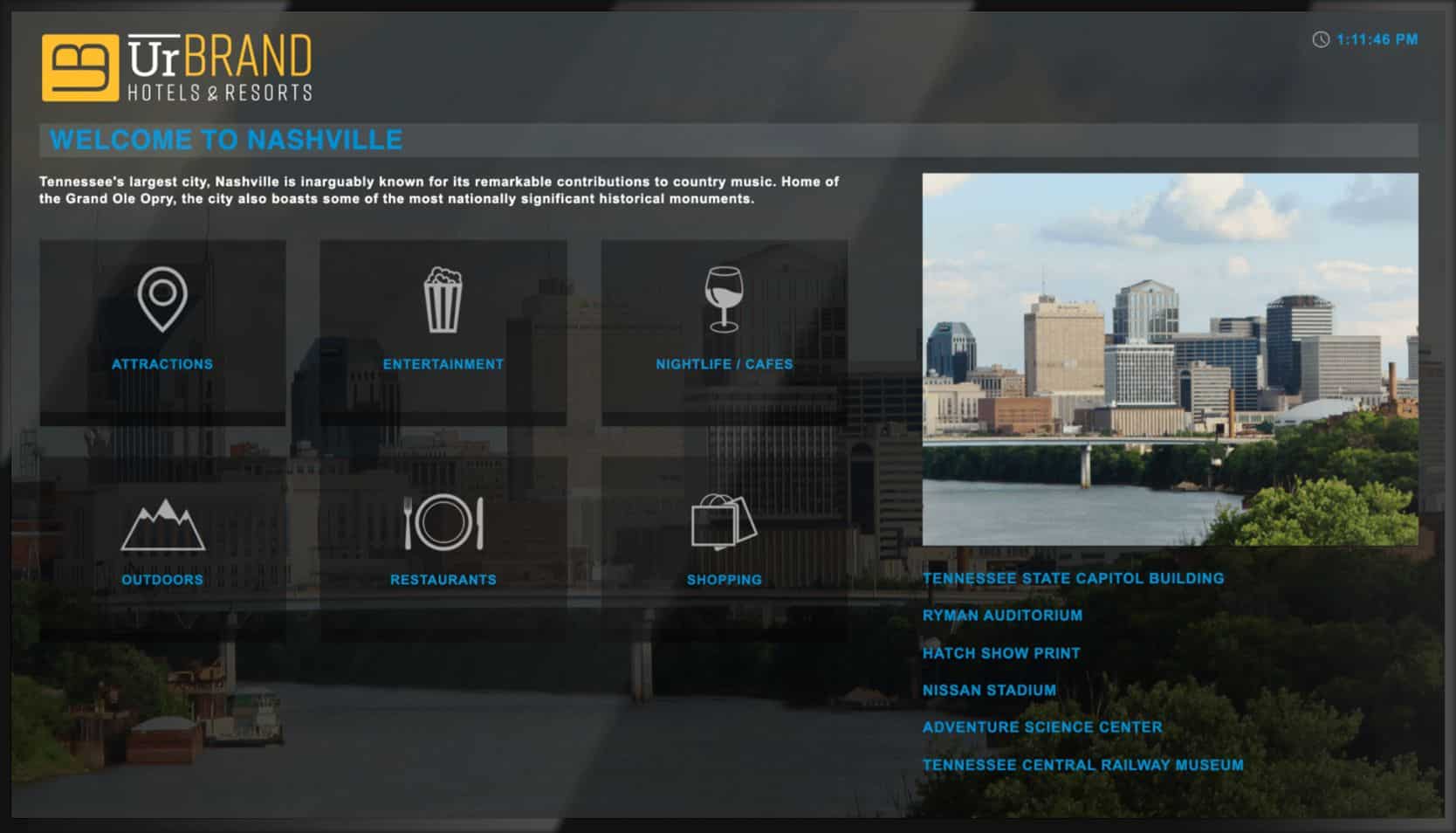
Digital Concierge
An all-in-one interactive digital signage platform that provides guests with local events, accommodation, and information on-demand.
Welcoming and property-branded user interface
Hosted on easy-to-use large format touch-screen devices with information such as attractions, entertainment, nightlife, shopping and more all tailored to your hotel’s location and branded to your property.
Comprehensive Venue Summary
Guests tap to explore an overview of attractions, nightlife and more – including costs, ratings, similar venues, phone numbers, hours of operation, and locations accompanied by an interactive map.
Points-of-interest Subcategories
Points-of-interest in the location community or city are neatly categorized so guests quickly find where to venture, including proximity, price range and peer ratings to help narrow results.
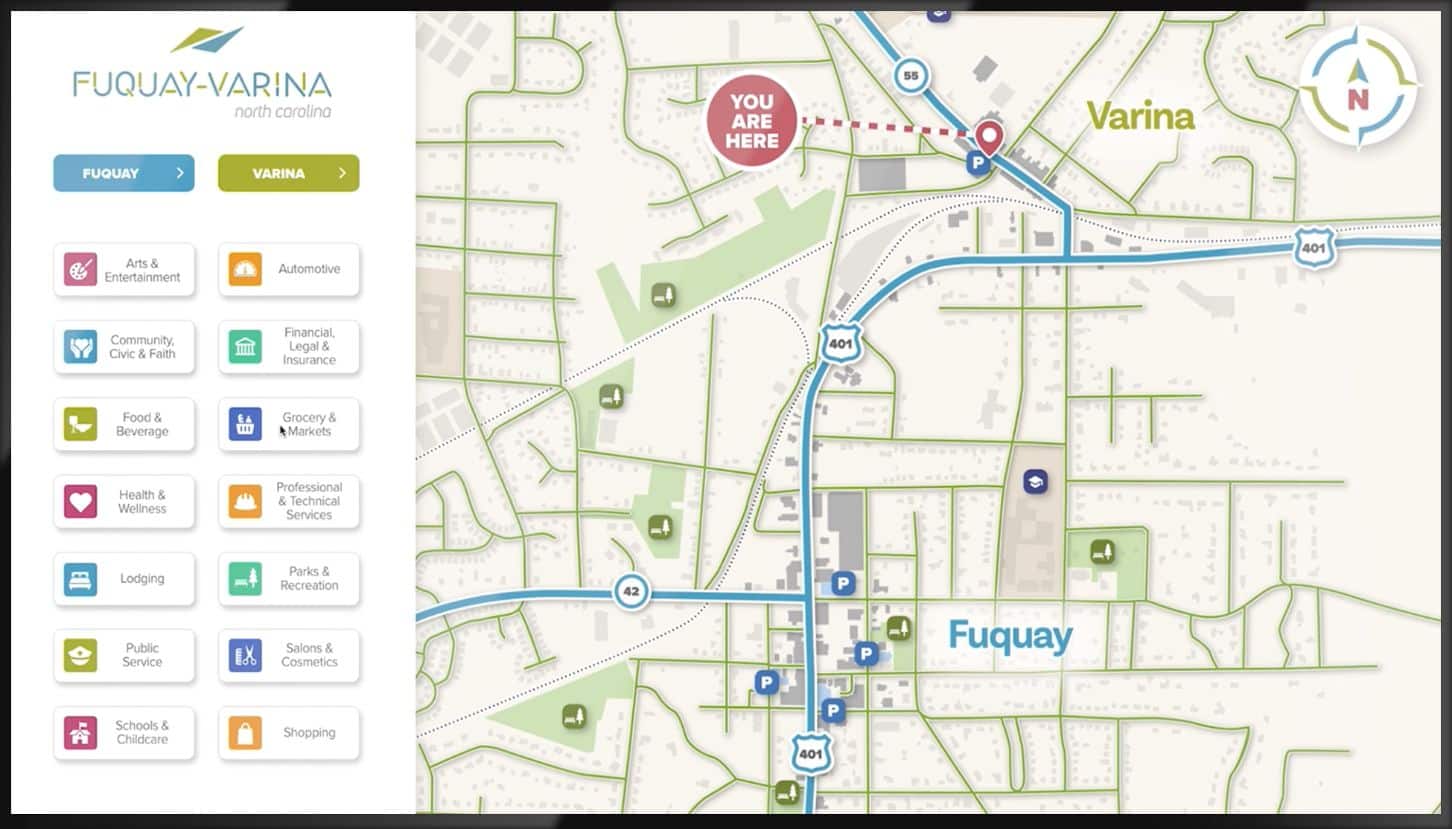
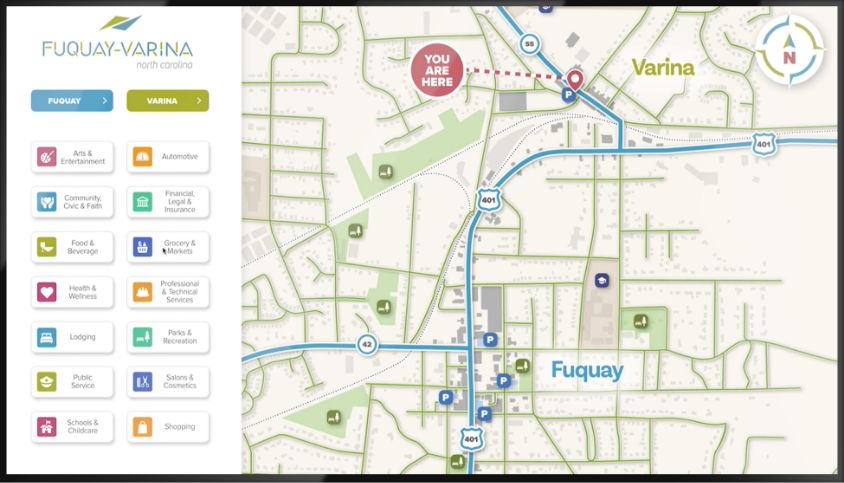
Wayfinder
Touchscreen digital wayfinder conveniently guides hotel guests to the right location, every time.
Guest Navigation
Help guests navigate to on-site amenities, restaurants or businesses.
Show Instructions
Show navigation instructions to on-property meetings, conferences of events.
Integrated Apps
Use integrate apps like local news, weather, and flight information.
Dynamic Content
Feature dynamic content like videos and interactive graphics.
Shuttle Tracker
Ease pressure on your team by displaying live real-time tracking of your shuttle service including current location, expected arrivals, and journey times.
Shuttle Tracker Map
The Shuttle Tracker map gives a real-time view of current shuttle locations.
Live Wait Times
Display live information including shuttle arrival and departure times, driving time, and wait times for ride share services (including Uber and Lyft).
Local Weather Forecast
The Shuttle Tracker gives your guests a 5-hour view of the local weather conditions.
Video Walls
We make it possible to implement the Video Wall of your dreams.
Create a completely unique, memorable experience that will set you apart from the rest and keep guests coming back for more.
Whether you want to create the ultimate information hub, an Instagram-worthy lobby installation or have even bigger dreams; we’ll make it happen!
No project is too big for us to implement or create.
Content Creation & Managed Services
We hear you — content takes time, resources, and effort your team might not have. That’s why our team of professional designers is here to help. We’ll set up a framework and layouts you can work within or build custom content to meet your brand guidelines. Or a little of both — you choose!
Scope and Discovery
As our client, you’ll meet with our professional services team to outline your digital signage design needs and objectives in a comprehensive project plan.
Collaboration and Design
Our team works collaboratively with yours to incorporate feedback and design new templates and content as needed to help you achieve your communication goals.
Deployment and Evaluation
We create branded templates or completely customized designs that your team can simply maintain with easy-to-update content zones.
Enclosures & Frames
We offer a wide variety of enclosures and displays to create the perfect combination
for any installation. Whether it’s a discreet screen at the elevators or an entrancing
full wall installation, we have the right hardware to implement your vision.
Options we offer to create your display;
- Zero bezel displays – Multiple zero bezel screens create stunning video
wall installations. - Touchscreen displays – Designed for interactive applications ranging from
10 to 95 inches. - Stretch Displays – Provide an extended width to fit naturally within
landscape or vertical orientation. - 4K Displays – Deliver UHD displays for maximum visual impact.
- Zero bezel displays – Multiple zero bezel screens create stunning video
Reliable hardware means a consistent experience with limited interruptions
Improve operational efficiency with high performing media players, commercial grade displays, and an enclosure to fit the vibe of every space.

Media Players and System-on-Chip (SoC)
Our solid-state Digital Signage Players offer feature-rich software and networking options for turnkey content management and delivery. Our content management system (CMS) also supports system-on-chip (SOC), allowing you to deploy digital signage without an external media player – simplifying implementation and reducing costs.
- Organize different media types (video, RSS, HTML, IPTV) into multiple
layers and zones to create a bespoke screen design. - Media players deliver full HD video playback or 4K content depending on
the model.
- Organize different media types (video, RSS, HTML, IPTV) into multiple